There’s been a lot of talk in the news lately about “encryption” that it’s starting to approach buzzword-level of use (see chart, below). 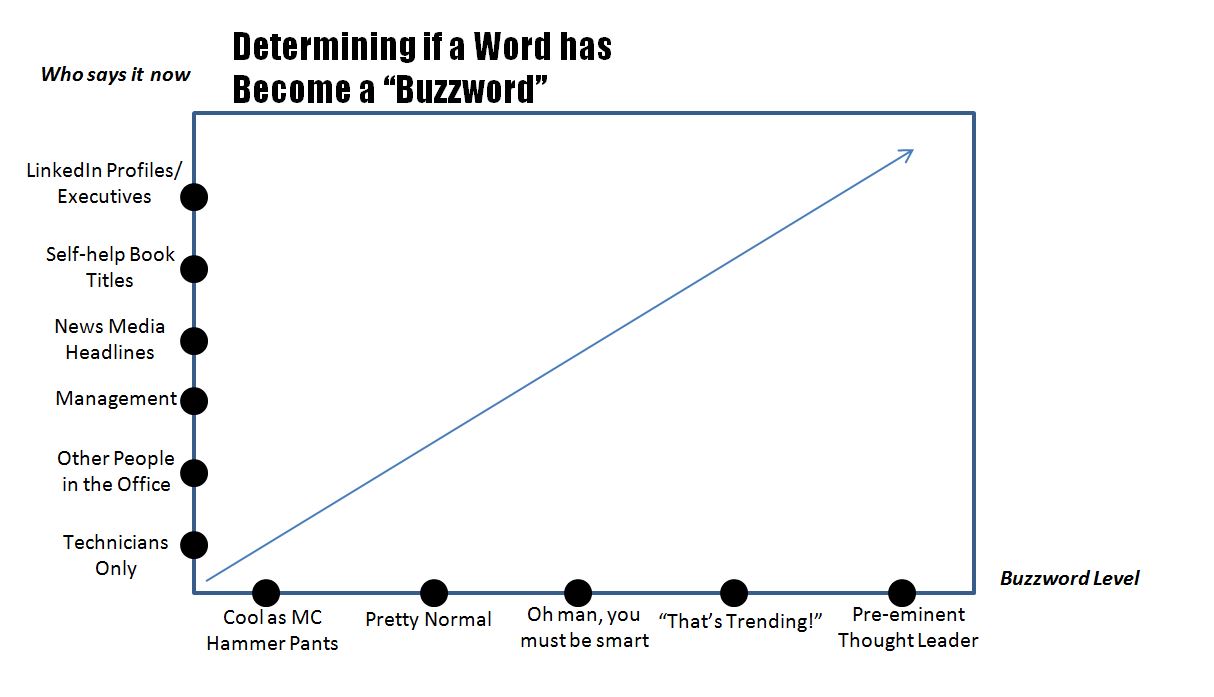
Encryption is essentially changing information to hide its original meaning. The opposite is decryption, where you make sense of encrypted information. Encrypted information is often referred to as the “cipher text.”
Basically, encryption is taking a piece of information and scrambling it so no one else except your intended audience can read and use the information.
Encryption = taking a piece of information & scrambling it so no one else except your intended audience can understand/read the information.
Now encrypted data (and data here means anything that’s been encrypted) can take the forms of other things called hashes. A hash is a one-way math machine that turns your information in to nonsense. The cool thing about this one-way math machine is there are enough variables at play that the only thing on earth that will ever produce the same value is that exact same input.
One example of this is the SHA1 hash. Heading over to sha1-online.com allows us to enter any text and click “hash” which will give us the SHA1 hash.
The only phrase that will ever create that unique hash is entering the phrase “Calibre Press For The Win!” Even entering an extra space after the exclamation point will give it a completely different hash value. That hash value is also known as a signature.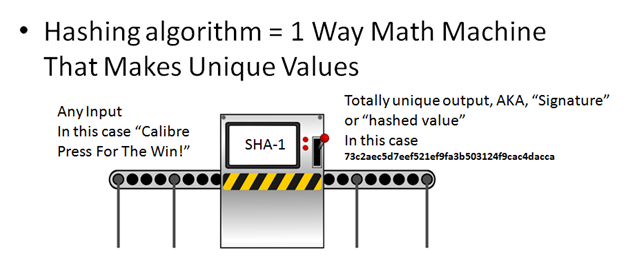
This is when everything is working right. The good thing about SHA-1 is that you can’t reverse that. You can’t take that signature and put it into some other math machine and reverse it to find out what the original input was.
The bad news is, you can just start making hashes of everything and creating your own library of phrases and data—or hashes. This is being done, and the hashes are being posted online so you can basically use the entire internet and Google to help you find out what a signature really is.
For example, if we Google our signature, it comes back with no results.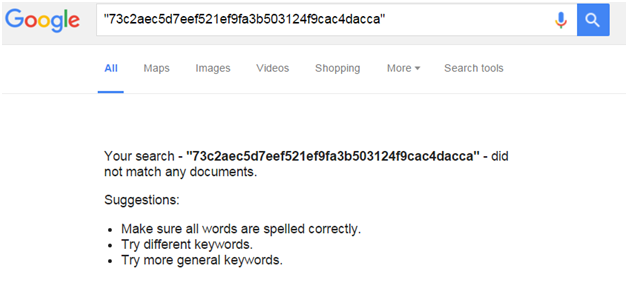
However, doing a Google search for a different hash value, 8be3c943b1609fffbfc51aad666d0a04adf83c9d, returns quite a few answers with the correct phrase: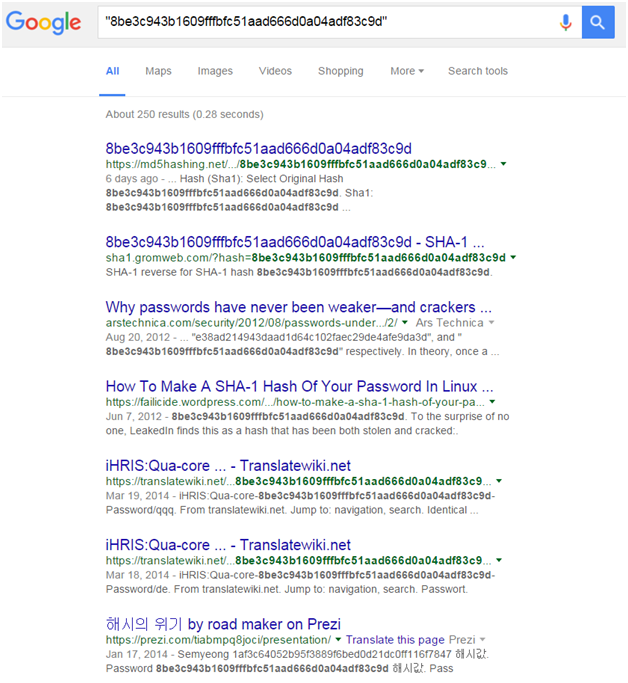
“Password,” one of the more common passwords out there, has been hashed and posted online quite a few times. Additionally, if we look for that hash in the website Pastebin (a well-known posting ground for data dumps) we’ll find website databases that have posted the usernames, email addresses, and hashed passwords for user accounts that have been dumped in data breaches.![]()
(Note: Victim’s email address blocked out.)
Add in the fact that users often use the same password on the breached website that they use for their email, and I know have the password to a lot of people’s emails!
Still don’t believe me? I just found this password hash: a5dfc157da97acb6b8262c2882250292f46d77dd. If we Google that, we get the answer almost immediately.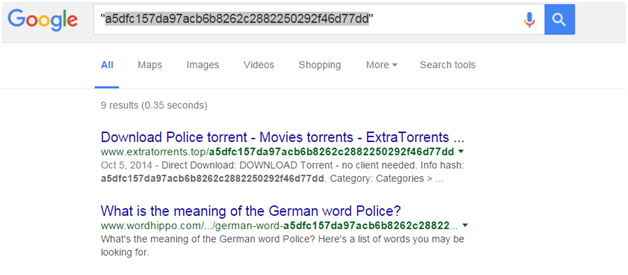
The second result has the answer in the question: “what is the meaning of German word Police.” We can quick verify that “Police” does produce that hash, and I have someone’s password based on their “encrypted hash.”
Even if something is encrypted, I can still cheat and find the key in new ways you never expected.
Use different passwords for your email from websites
Yes my friends, simply saying something is “encrypted” is no longer good enough. We keep asking if something is “encrypted” as if it’s magical bacon bits that makes everything better and perfect.
No, it is not. How it’s implemented makes a biiiiiig difference.
This is where taking the time to train yourselves, and your staff, to understand the difference between good encryption and bad encryption is quickly becoming worthwhile. We incorporate all this stuff into our work, yet we don’t understand how it works and how it’s flawed. Simple things like this make all the difference.
Conclusion
Training, training, training! Yes, you need to train some one to understand this stuff. The world we live in requires it. This is really simple.
And of course, use different passwords for every site you have an account. But you do that already, don’t you?










0 Comments